
N‑able EDR Mitigate ransomware at lightning speed

42% of the most frequent attacks MSPs are seeing are ransomware-led.* Detect and respond to cybersecurity threats in seconds, not hours, with N‑able Endpoint Detection & Response.
* State of the Market: The New Threat Landscape. Pushing MSP Security to the Next Level, N‑able report, March 2022
*Terms and conditions apply.
Why customers choose N‑able EDR
“The SentinelOne EDR solution, integrated with N‑central, has simplified our approach to providing our clients with a comprehensive endpoint security solution that we can trust, and is a requirement for all of our customer endpoints.”
AI-based ransomware
protection
Automated threat
response
Behavioral AI
detection engines
One-click remediation
and rollback
Threat intelligence
and indicators
Incident forensics
reporting
Minimize cybersecurity risks. Cut unnecessary costs.
82% of MSPs’ customers have seen an increase in attempted cyberattacks
State of the Market: The New Threat Landscape Pushing MSP Security to the Next Level, N‑able report, March 2022
82% of MSPs’ customers have seen an increase in attempted cyberattacks
State of the Market: The New Threat Landscape Pushing MSP Security to the Next Level, N‑able report, March 2022
Increase efficiency with integrated security
Increase efficiency with integrated security
Access EDR from your N‑able™ N‑central® or N‑sight™ RMM dashboard. Create rules-based policies and deployments. Remediate threats with no endpoint scans or signature definition updates.
Easily prove value to your customers
Easily prove value to your customers
Offer more robust protection and faster incident response than traditional AV. Show how you’re keeping clients safe with straightforward attack visualizations and forensics reporting.
Accelerate threat incident response
Accelerate threat incident response
Minimize downtime risks with a team of one. Rapidly contain threats and automatically remediate malicious changes. Roll back devices in seconds in case of ransomware.
Demonstrate safe business to insurers
Demonstrate safe business to insurers
Strengthen your security posture with state-of-the-art EDR technology. Demonstrate safe business to help keep your cybersecurity insurance costs down.
Elevate your business with dedicated resources
Elevate your business with dedicated resources
Access endpoint security resources, knowledge, and best practices via the Head Nerds, the N‑able MarketBuilder, the MSP Institute, and more—all at your disposal, within easy reach.
Easily deploy EDR
Provide protection with staying power. Create and deploy policies, typically in minutes, so you can monitor and manage your customers’ endpoints. Leverage powerful EDR integration with the N‑able N‑sight RMM or N‑able N‑central solutions to gain holistic monitoring and management capabilities.

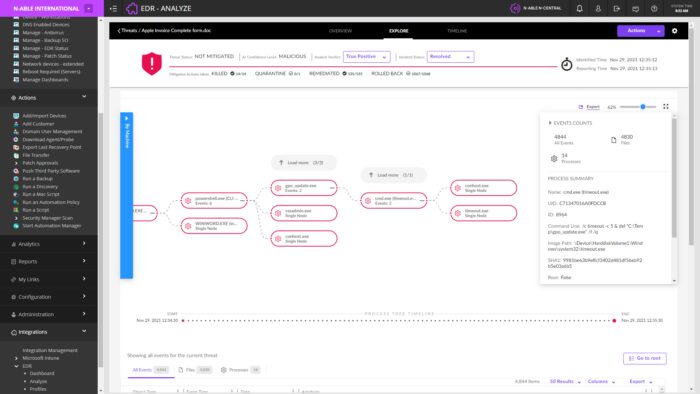
Analyze any cybersecurity threats
Use automation and AI data points to identify threats and determine how to respond. The threat overview and timeline visualizations empower your techs to analyze attacks while showing your customers how you’re safeguarding their devices.
Roll back devices when ransomware strikes
Prove the worth of your security service when ransomware strikes. Roll back infected devices (Windows OS only) to their pre-infected state typically in minutes, even seconds—not hours. Help your clients avoid costly outages, data loss, and ransoms. Give them the peace of mind that they can run their business—while facing down cybersecurity threats.
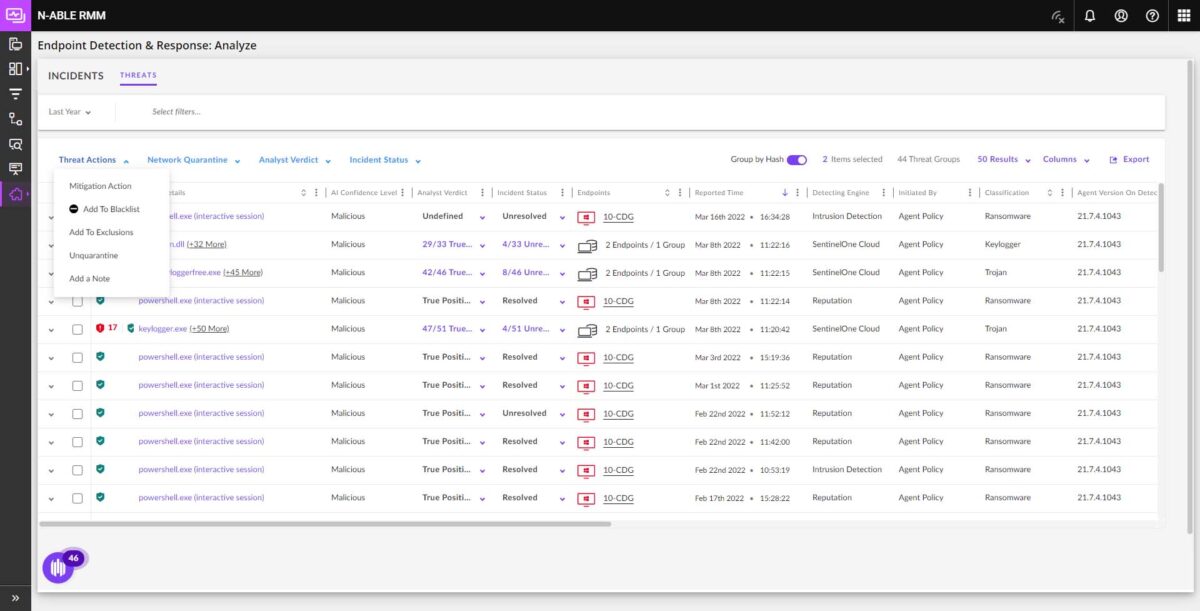
Upgrade traditional AV
Upgrade your endpoint protection to defend against evolving threats. Use EDR to respond to threat incidents 3x faster than with traditional AV. Minimize tech time while maximizing their effectiveness: a win-win for you and your clients.
Why N‑able EDR

SentinelOne®—the technology behind N‑able EDR—excelled in every category of the 2022 MITRE Engenuity™ ATT&CK® Evaluation. With a 100% prevention score, it recorded the highest number of analytic detections with zero detection delays.* Read more
* Source: 2022 MITRE Engenuity™ ATT&CK® Evaluation.
“Tech Solutions deploys N‑able Endpoint Detection and Response (EDR) because with today’s ever-evolving threats, antivirus isn’t enough. EDR can not only stop ransomware in its tracks, it also allows us to roll back to the pre-infected state. We can’t recommend it highly enough to businesses of all sizes.”
“With multiple AI engines at work, we never have to worry about existing malware, let alone zero-day threats. It’s incredibly easy to deploy, and it can be completely automated. And we can not only protect our customers but show them what happened in an attack with the rich storyline capability.”
“I’ve recently started using EDR. One of the most important features to me is how it can roll back a device if it does detect something malicious, without me even having to touch it. This ticks one of my big fears…an attack could take a long time to fix, and my customer would be down. This is a really, really good feature.”
Uplevel your endpoint security
Threat Hunting
Get deeper visibility into your endpoint data to uncover indicators of compromise.
Resources
Endpoint Detection and Response Standalone Datasheet
MITRE Engenuity ATT&CK evaluation
N‑able EDR and SentinelOne deliver for Ballast Services
Five Cyberthreats that Slip Past Traditional Antivirus eBook
Want to learn more about N‑able EDR?
N‑able EDR helps you manage and prevent sophisticated attacks with next-generation threat protection. Connect with our experts to learn more.
