The Email Security Education Series: What Does a Phishing Campaign Look Like?

Please note: For privacy reasons the identity of the hacked account in the example used for this blog has been changed.
In our previous email security education blog we reviewed trending email security threats. In this blog we’d like to show you what a phishing campaign looks like, and its scary consequences.
 Bad actors (hackers, spammers, scammers, etc.) care about the numbers—the more data they have the better the chances of success and financial gain. They use a variety of methods to get your email address, from using “publicly available” cheap lists and exploiting websites to obtain data dumps to using scraping software to harvest email addresses from thousands of web pages. They can easily get a million email addresses to use in their phishing campaigns.
Bad actors (hackers, spammers, scammers, etc.) care about the numbers—the more data they have the better the chances of success and financial gain. They use a variety of methods to get your email address, from using “publicly available” cheap lists and exploiting websites to obtain data dumps to using scraping software to harvest email addresses from thousands of web pages. They can easily get a million email addresses to use in their phishing campaigns.
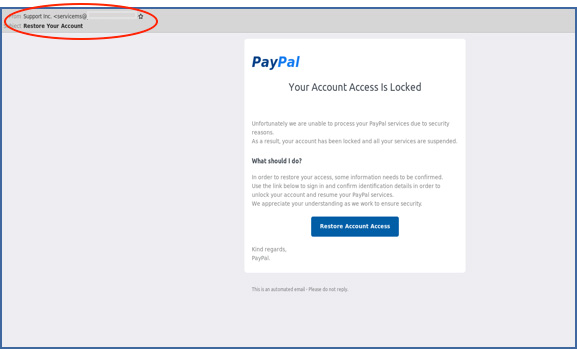
In this example, the hackers are pretending to be PayPal, informing users their account access has been locked and the account suspended due to security reasons. To restore account access, they request users click on the link in the email to confirm their personal details.
So how do you spot this is a phishing email?
In the “From” field notice that the sender is not a standard PayPal address, but: “servicems@xxx”. Clicking on the link takes you to the following site:
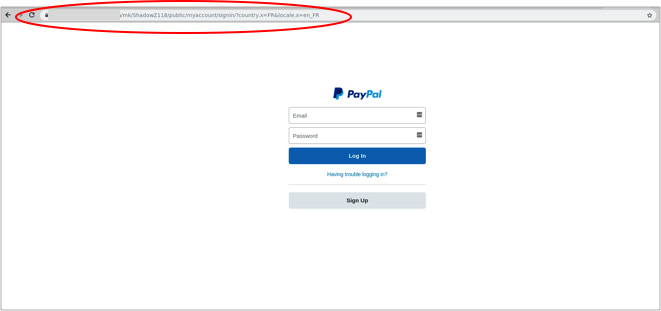
While this may look like a PayPal page, notice the URL: “mk/ShadowZ118/public/myaccount/signin/?country.x=FR&locate.x=en_FR”. If this had been PayPal, you would have seen a legitimate PayPal URL.
Looking at the email headers (view email headers) in the image on the right will also show telltale signs that this is not a legitimate PayPal website. For example, below:
 X-PHP script of “senddd.php” is not something that PayPal would ever use
X-PHP script of “senddd.php” is not something that PayPal would ever use- X-PHP Filename would indicate that it’s a different PHP script that sent the actual email
- X-Message ID does not show the typical “@PayPal.com” part
- Received headers do not show the legitimate PayPal servers
Here is an example of what the “senddd.php” looks like. As you can see this is a standard PHP custom mailing script that comes in all shapes and sizes, where the bad actors are able to set the subject, from, and content fields to anything they desire. In the “Maillist” field the hacker will add an entire list of email addresses found using one of the methods mentioned above (e.g. scraping). Normally the email server does not belong to them, and hence they don’t care if it gets blacklisted.
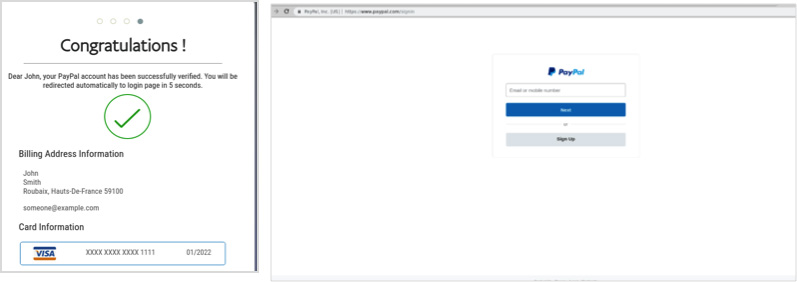
When users log in to the fake “PayPal site” and continue to complete all their account and personal information (see below screenshots) the bad actors get access to all their information, which is auto saved on the site the bad actors use. This is an example of an advanced phishing kit, where not only basic information is requested but also passwords, credit card information, and screenshots of passports.
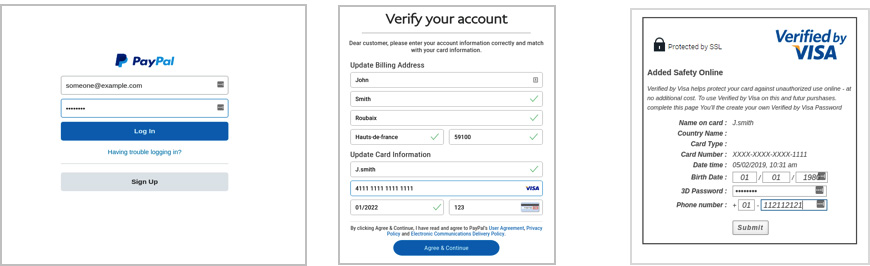
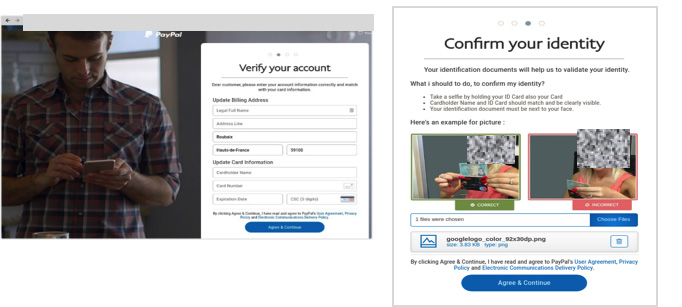
As users complete their credit card information the bad actors save all the information in the back end with the help of a little PHP script. Looking closely at the script in the image below, we can see the scammers are saving all the vital information they need to commit fraud then simply sending all the information to their own email address.

Finally, users receive a confirmation that their account has been successfully “verified,” and are automatically redirected to the PayPal official site. Meanwhile, the bad actors have saved their personal information, including credit card numbers, passport photos, and relevant passwords—all that is needed for the bad actors to inflict damage.
As seen in this blog, acting on phishing emails could have severe consequences. With that in mind, here are four steps you can take to help protect yourself:
- Always check the URL
When in doubt, DO NOT click. Hover your mouse over the link to see where the link directs to. If the address showing in the hovered link is not the same as the address it says it is, DO NOT click on it. If you accidentally click on the link, don’t enter any information on the website; simply close the browser window. - Lookout for malicious email attachments
Be careful when receiving email attachments. It is important to remember not to blindly open attachments; check the file first by saving it to your downloads folder. Next, make sure if you are using Windows to set your folder options to “show known file types” so you can view the file extension (e.g. the three letters at the end of the file name). Unzip the .zip file from your downloads and view the file extension. If it contains any of the following: .JS, .EXE, .COM, .PIF, .SCR, .HTA, .vbs, .wsf, .jse, or .jar at the end of the file name it is malicious and you should not click on it or try to open it. - Add powerful email security
Solutions like SolarWinds® Mail Assure can help you safeguard your email from phishing attacks. Leveraging collective intelligence for inbound and outbound email security, Mail Assure uses data gleaned from monitoring more than 2 million domains under management. This data feeds into our intelligent protection engine to combine with near real-time, pattern-based threat recognition and a variety of filtering technologies to help protect against spam, viruses, ransomware, malware, phishing attacks, and other email-borne threats. - Set-up SPF, DKIM, and DMARC
As part of an email security solution, you can take additional steps and set up SPF, DKIM, and DMARC. SPF (Sender Policy Framework) is used to restrict which mail servers can send email for a specific domain name. This framework is designed to detect and block email spoofing by providing a mechanism to allow receiving mail exchangers to verify that incoming mail from a domain comes from an IP address authorized by that domain’s administrators. DKIM is a method used to sign your outgoing emails to allow the recipient to verify that the messages originated from the specified sender, and that the message content has not been altered. Finally, DMARC (Domain-Based Message Authentication, Reporting and Conformance) is an email protocol designed to help prevent email spoofing when used in conjunction with SPF and/or DKIM.
If you are looking to protect email against phishing attacks, including other email-borne threats, start a trial with SolarWinds Mail Assure today and see how we can help keep your inboxes clean.
If you’re looking for email security made affordable and reliable, SolarWinds® Mail Assure™ cloud email security for Office 365 is your answer. Why not give it a try?
Mia Thompson is product marketing manager, Mail Assure at SolarWinds MSP.
Want to stay up to date?
Get the latest MSP tips, tricks, and ideas sent to your inbox each week.
